Malware analysis Malicious activity
Por um escritor misterioso
Descrição

Routers Roasting on an Open Firewall: the KV-botnet Investigation

A detailed analysis of the Menorah malware used by APT34
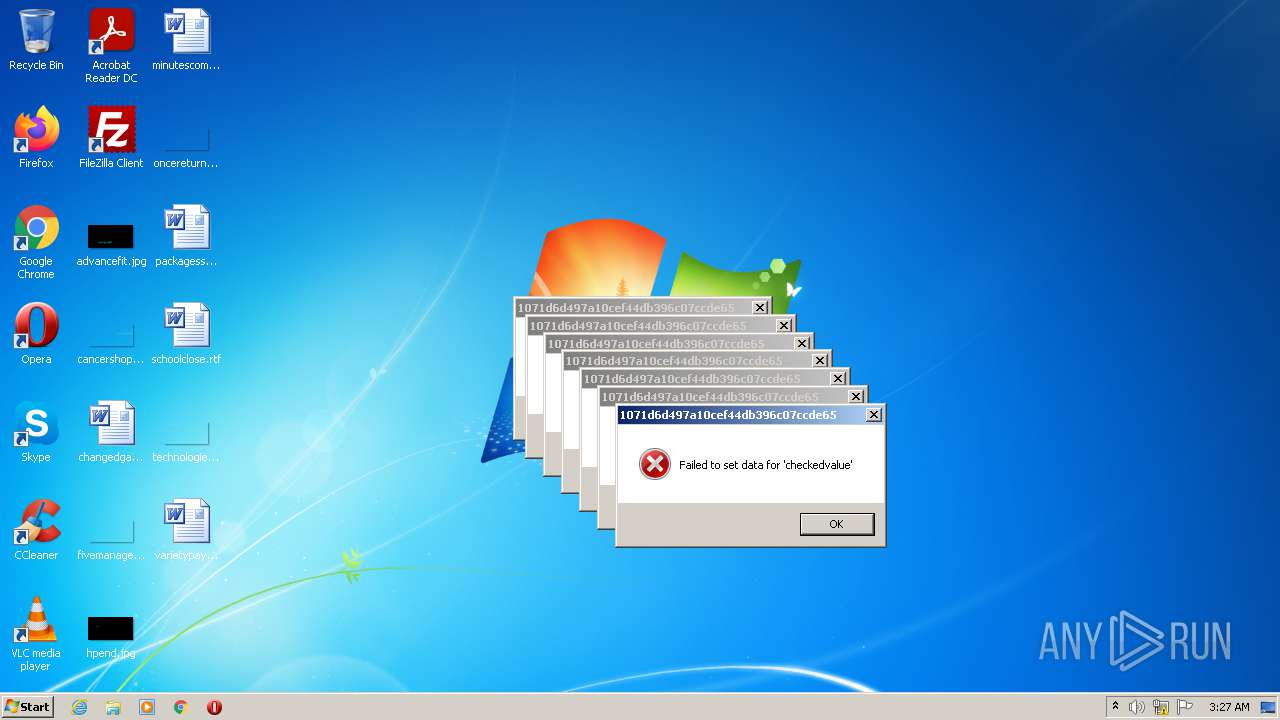
Malware analysis 1071d6d497a10cef44db396c07ccde65 Malicious

Malware Analysis: Steps & Examples - CrowdStrike
Krebs on Security – In-depth security news and investigation

PROUD-MAL: static analysis-based progressive framework for deep

Endpoint Detection and Response, Free - What is EDR Security?

Malware Analysis: Steps & Examples - CrowdStrike
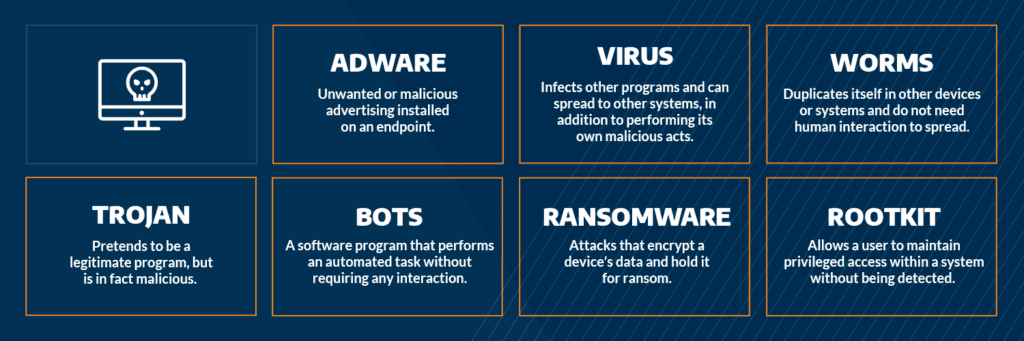
Most Common Malware Attacks

Remediation and Malware Detection Overview

PROUD-MAL: static analysis-based progressive framework for deep
de
por adulto (o preço varia de acordo com o tamanho do grupo)







